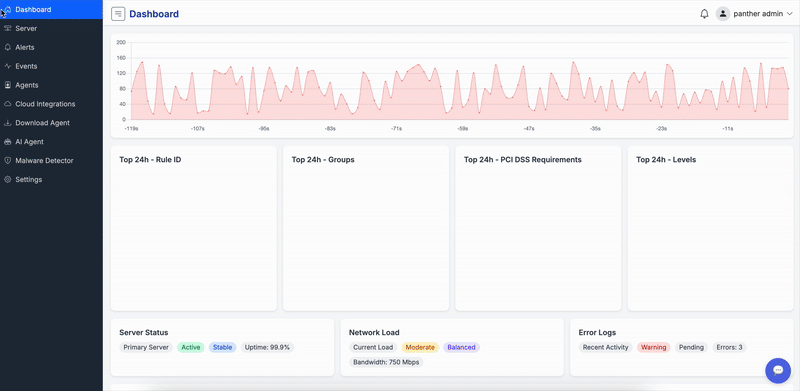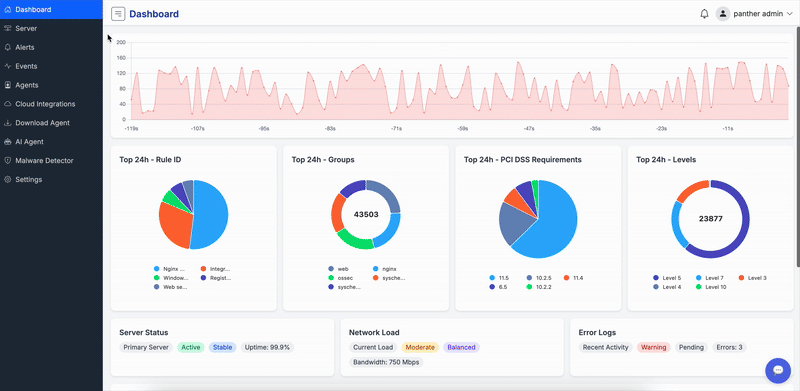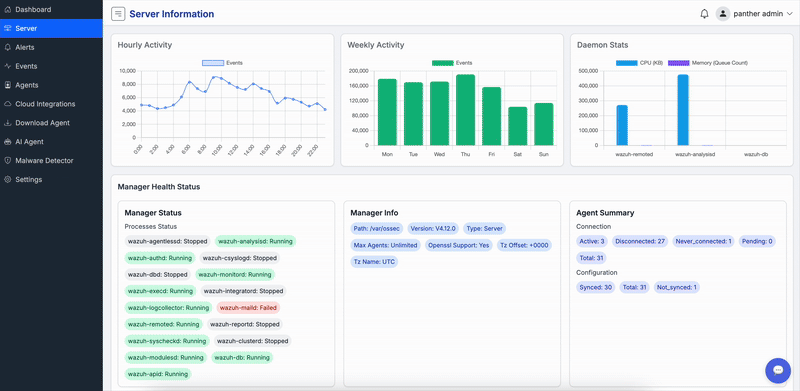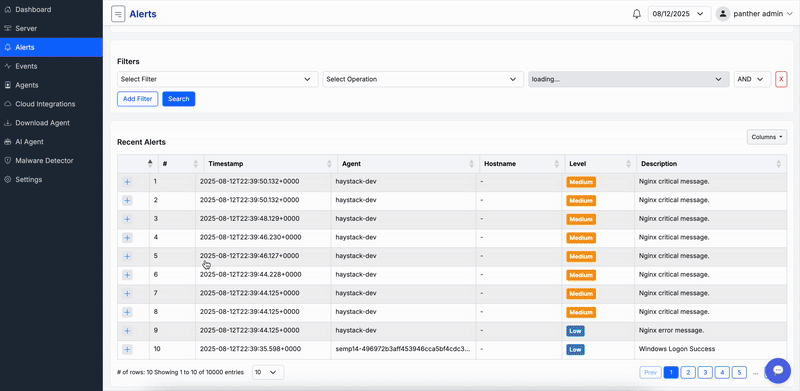
Digital Forensics Meets Real-Time Threat Intelligence
ForenSyc combines advanced digital forensics with AI-powered threat detection to protect cloud environments, endpoints, and critical assets. Investigate incidents, analyze malware, and respond to threats with enterprise-grade security intelligence.
Get started with enterprise-grade security in four simple steps
Seamlessly integrate with cloud providers, endpoints, and security tools in minutes with one-click deployment.
Customize threat detection policies, compliance rules, and automated response playbooks for your organization.
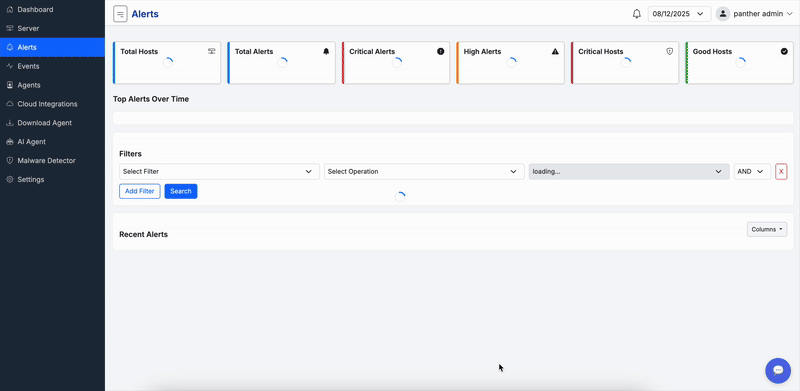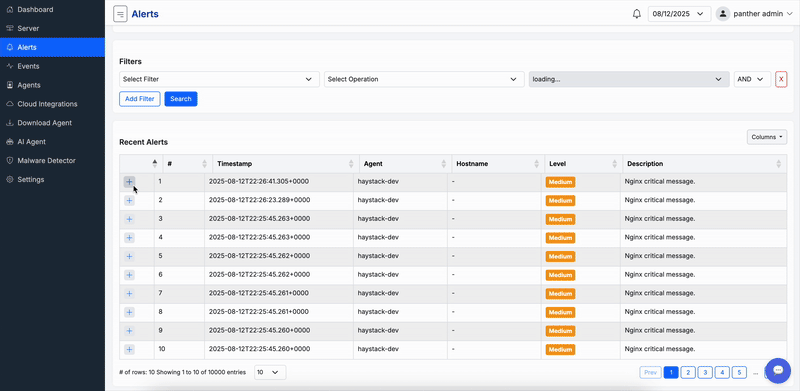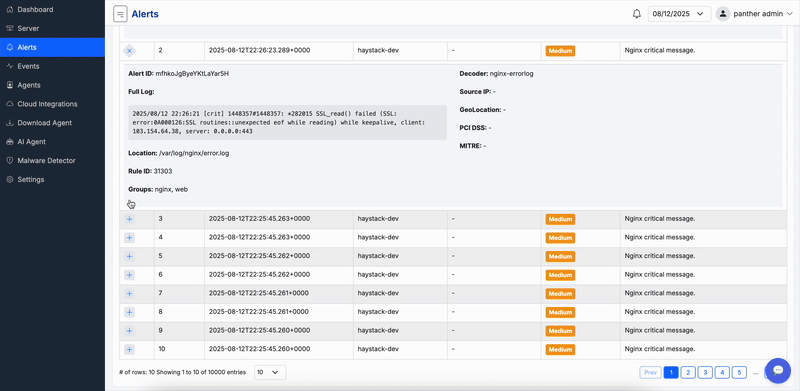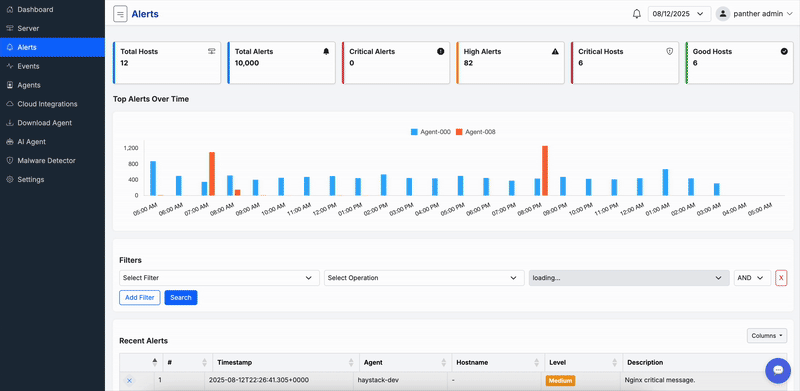
Real-time threat monitoring with AI-powered anomaly detection and advanced forensic investigation tools.
Automated incident response with customizable playbooks. Contain threats instantly with detailed audit trails.
Built for security teams who need comprehensive threat detection, incident response, and digital forensics in one unified platform
Advanced forensic analysis capabilities for in-depth incident investigation and evidence collection.
Multi-cloud threat detection with real-time monitoring for AWS, Azure, GCP, and hybrid environments.
Comprehensive EDR with behavioral analysis for Windows, macOS, Linux, and mobile devices.
Advanced malware detection using static, dynamic, and behavioral analysis techniques.
Automated workflows and playbooks for rapid threat containment and remediation.
Centralized log management with advanced analytics and threat hunting capabilities.


























Experience the power of ForenSyc through live demonstrations of our security platform
Scan endpoints, servers, and IoT devices for vulnerabilities, malware, and anomalous behavior with real-time monitoring and endpoint detection and response (EDR) capabilities.
Features include remote quarantine, patch management integration, and forensic logging for incident investigation. Supports Windows, macOS, Linux, and mobile devices with minimal performance impact.
Receive instant notifications via email, SMS, Slack, or webhooks for suspicious activities, with customizable thresholds, escalation rules, and suppression to reduce noise.
Includes interactive dashboards for alert history, resolution tracking, and analytics to identify patterns. Integrate with ticketing systems for automated workflows and faster response times.

Monitor cloud assets for misconfigurations, unauthorized access, data exfiltration, and compliance violations using AI-powered anomaly detection and baseline profiling.
Supports multi-cloud environments with automated remediation suggestions, policy enforcement, and detailed forensic reports. Detects advanced persistent threats (APTs) and zero-day exploits through behavioral analysis.
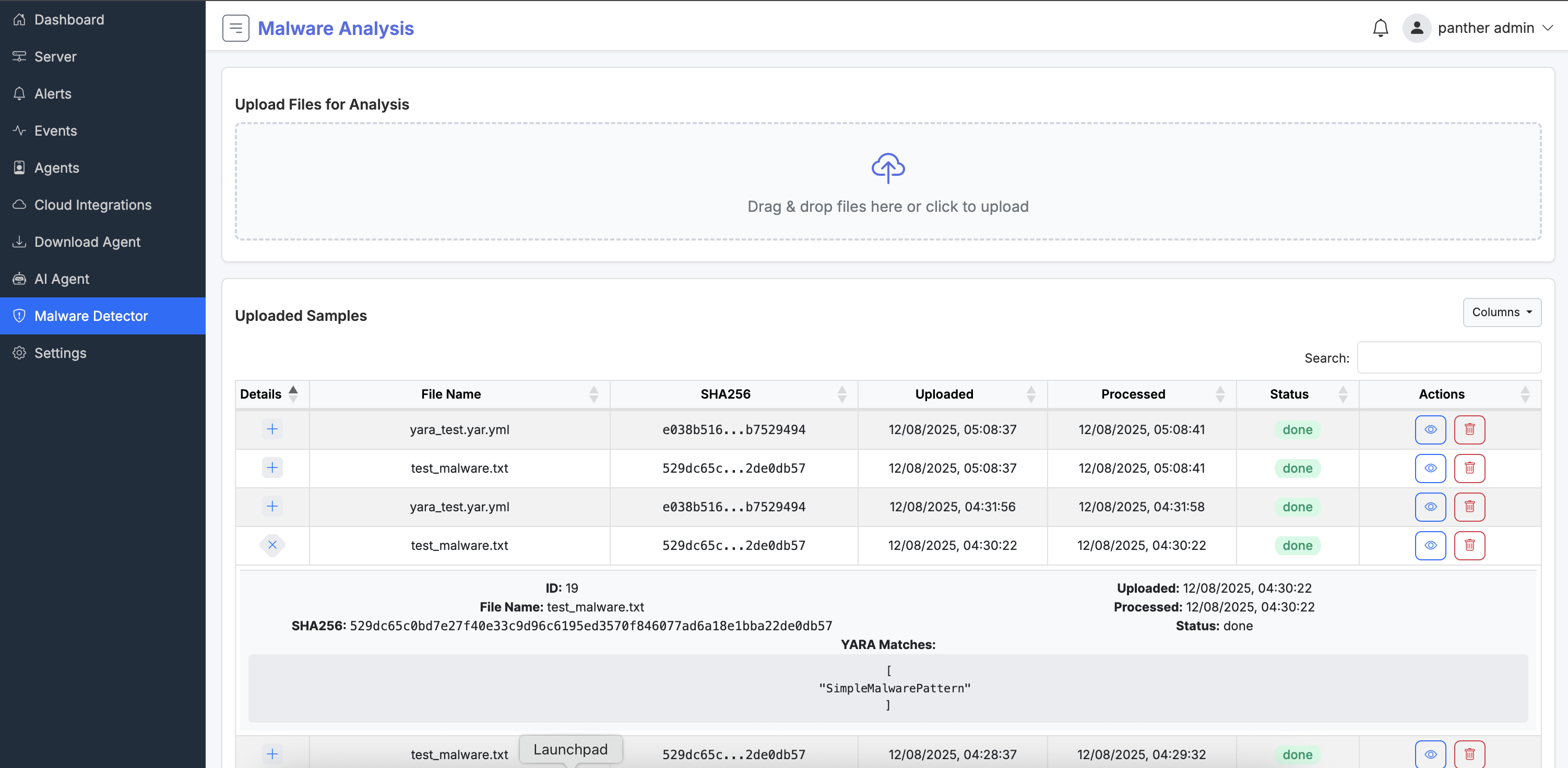
Analyze files, executables, and network traffic for malware using signature-based, heuristic, and machine learning methods, supporting on-demand scans, scheduled checks, and API integrations for CI/CD pipelines.
Includes sandboxing for suspicious files, detailed threat intelligence reports on vectors, payloads, and mitigation steps. Continuously updated with global threat feeds for emerging malware variants.
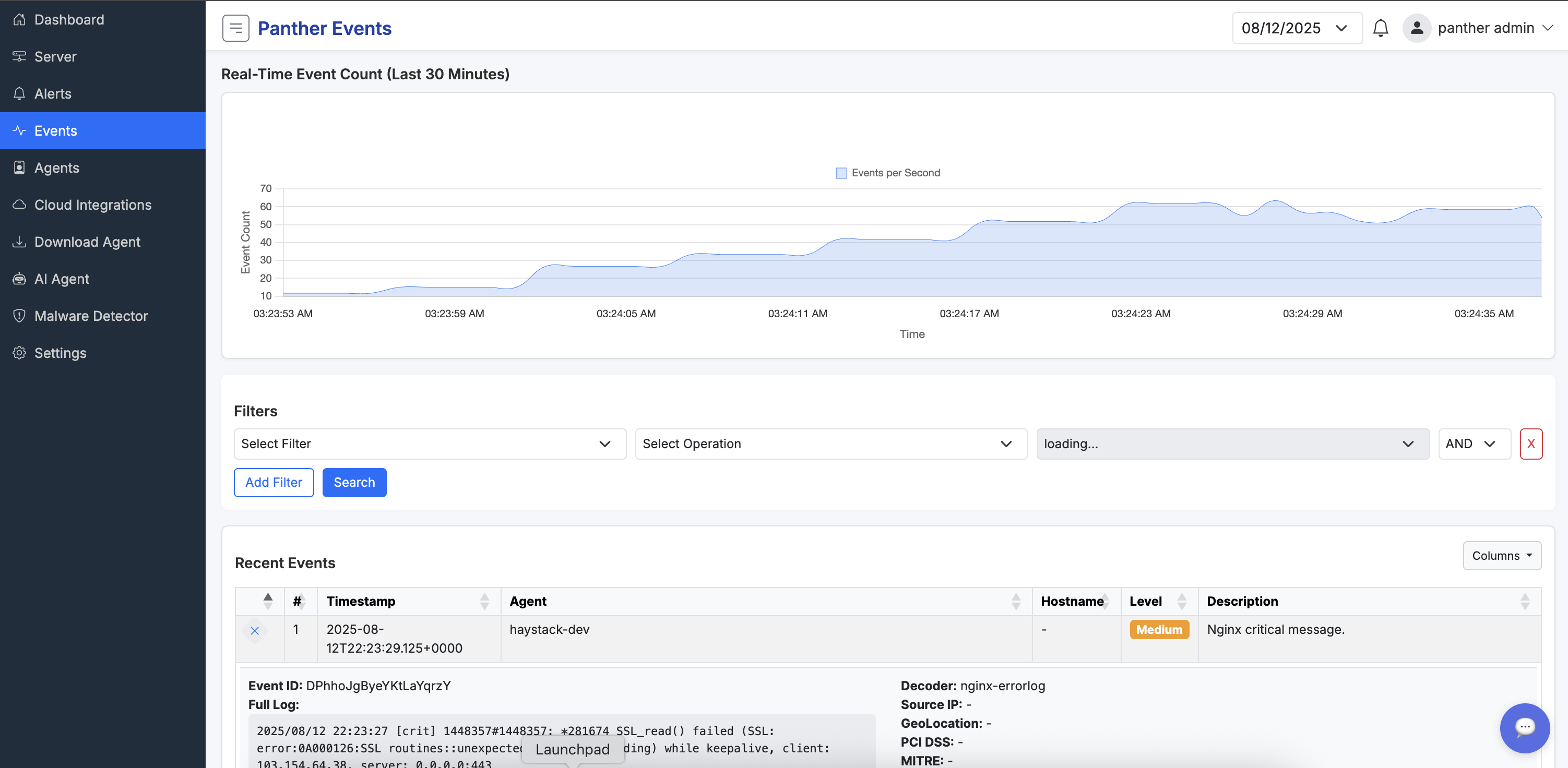
Centralize logs from clouds, devices, and applications for efficient querying, visualization, and long-term storage. Supports customizable retention policies, advanced search filters, and integration with SIEM tools for enhanced correlation and reporting.
Benefit from real-time log ingestion, anomaly detection within logs, and export options for compliance auditing. Our system handles petabytes of data with high performance, ensuring no loss of critical information.
Tailored security solutions for organizations across all sectors
Meet strict regulatory requirements while protecting sensitive financial data from sophisticated threats.
Protect patient data and ensure HIPAA compliance with advanced threat detection and forensics.
Secure your SaaS infrastructure and customer data with comprehensive cloud security monitoring.
Protect customer transactions and prevent payment fraud with real-time threat intelligence.
Safeguard student data and research while maintaining open collaboration environments.
Meet stringent security standards with FedRAMP-ready infrastructure and advanced forensics.
Flexible pricing designed to scale with your organization's security needs
Multi-cloud threat detection and compliance monitoring
Complete EDR with forensic investigation capabilities
Advanced threat analysis with sandbox and ML detection
ForenSyc's forensic capabilities helped us identify and contain a sophisticated APT attack within hours. The timeline reconstruction and evidence collection features are unmatched.
The cloud security monitoring has been a game-changer. We reduced our mean time to detect (MTTD) by 85% and gained complete visibility across our multi-cloud infrastructure.
The malware analysis platform caught zero-day threats that our previous solutions missed. The automated sandboxing and detailed IOC extraction saved our team countless hours.
Join thousands of organizations protecting their digital assets with ForenSyc. Start your free 14-day trial today.
Connect with our team for a personalized platform demonstration